Due to recent vulnerabilities being discovered in ssh clients, the University of Delaware made important security updates Jan. 19, 2016. As a result, new keys for several hosts that accept ssh or sftp connections were generated (newer, longer (2048 bit), and stronger keys), and newer versions of ssh server software was installed.
As result of these changes, many people will need to be prepared to make changes to how they connect to central UNIX servers.
Jump to Secure Shell (Win) | WinSCP and PuTTY (Win) | Linux and Macintosh | Other software
Back to Top
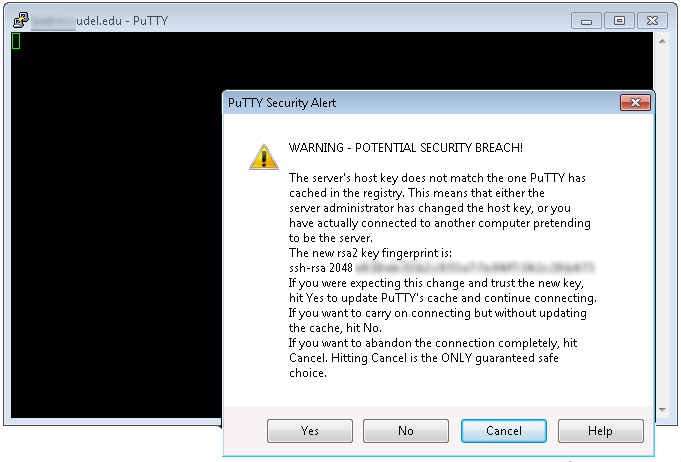
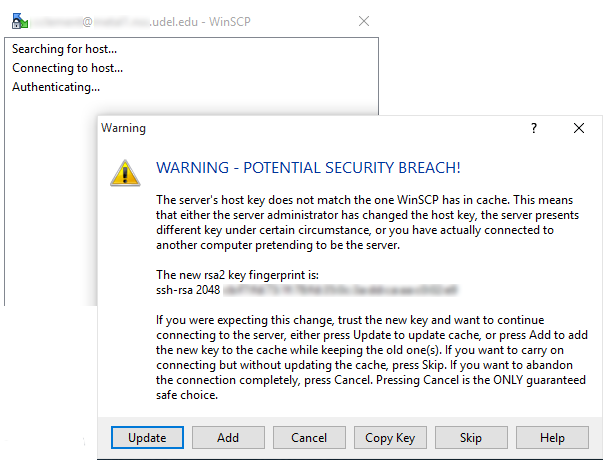
People who are already using WinSCP and PuTTY may see a warning message titled WARNING – POTENTIAL SECURITY BREACH advising them that the key has changed.
After looking in the WinSCP or PuTTY screen's toolbar to be sure
you are connecting to the known UD host you intended to, confirm the
connection by clicking Yes or Update. (Screenshots below)
Back to Top
ssh-keygen -R hostname-entry-to-remove
The first time you connect to a host, you'll have to accept the new key. The worksession below shows the process as captured from one Macintosh user's terminal window. (Some information edited. Bold indicates what the user typed before pressing the ENTER of RETURN key.)
JohnMac$ ssh-keygen -R copland.udel.edu /Users/john/.ssh/known_hosts updated. Original contents retained as /Users/john/.ssh/known_hosts.old JohnMac$ ssh copland.udel.edu The authenticity of host 'copland.udel.edu (128.175.13.92)' can't be established. RSA key fingerprint is xx:xx:xx:xx:xx:key:sc:ra:mb:bl:ed:xx:xx:xx:xx. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'copland.udel.edu' (RSA) to the list of known hosts. johnmacx@copland.udel.edu's password: copland.udel.edu%
Back to Top
If you use software that connects to a central UNIX server to transfer files, you may have to re-configure that software or accept a new key from the remote host.
As an example, here is information about using DreamWeaver.
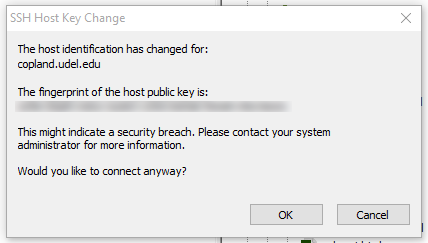
Reminder: This page uses DreamWeaver as an example. Other software that relies on an sftp or ssh connection may have different methods of configuring the software properly.
Back to Top
 Search for forms & applications.
Search for forms & applications.