Take a BITE out of phish!
Monthly Phishing Campaign Program
When it comes to spotting phishing emails, practice makes perfect. Phishing awareness and reporting exercises are designed to give the UD community experience in identifying and reporting simulated phishing emails that come from actual real world examples.
Why do phishing tests?
1. Phishing is the single greatest threat to digital privacy and security (+)
According to industry studies:
- 90% of data breaches are the result of phishing. (Source)
- 85% of cyber attacks rely on social engineering, and 60% of the time this is done through phishing emails. (Source)
- Despite enhanced security measures, in 2021 US workers received an average of 14-49 malicious emails per year, and that number is increasing each year. (Source)
UD's 2013 cyberattack exposed more than 72,000 people to identity theft. The stolen data included names, addresses, Social Security numbers, and university identification numbers of current and past employees, including student workers and school officials.
UD security systems block millions of phishing messages each month, but some will always make it through. The best defense against these malicious emails is a user community made aware of the current phishing tricks and trends through regular practice.
2. Phishing simulations decrease susceptibility to attacks (+)
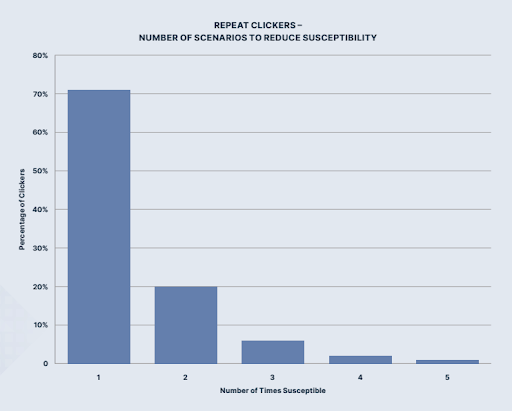
A cyber security report – 2022 Annual State of Phishing Report, has analyzed millions of campaign results from users who have received simulated phishing training. The research found that repeated phishing simulations have been a helpful way to help employees spot malicious emails and hence, reduce their susceptibility. 70% of respondents were susceptible during their first encounter with a simulated phishing email. After simulations have been deployed 5 times, the percentage of susceptibility dramatically dropped to a single digit. A higher frequency of phishing simulations increases the ability to recognise phishing emails.
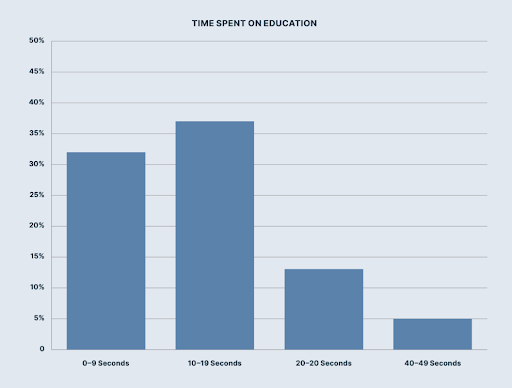
The report has also pointed out that users who clicked on a fraudulent link had one thing in common – they spent very little time checking the landing page of the phishing simulation. The average time spent was just 0-19 seconds according to the research. This implies the fact that the more time the staff are willing to spend on phishing education, the more capable they are to find out the red flags in a simulated phish.
The above standpoint is further assured by Microsoft's Digital Defense Report 2022. A popular website for cybersecurity news sources has quoted the finding from Microsoft, stating that “when employees receive simulated phishing training, they’re 50% less likely to fall for phishing.”
3. Simulated phishing exercises increase reporting rates and responsiveness (+)
The annual state report we previously mentioned showed that 82% of trained employees reported simulated phishing. More amazingly is that they reported it within 60 minutes of receiving it. Timely user reporting not only decreases the window of opportunity that an adversary has to access data or gain further network entry but also increases the opportunity the security team has to detect and respond to potential breaches. The success of simulated phishing is further confirmed by another industry research, which indicates that after completing one year of phishing awareness training, the average phish-prone percentage sharply dropped from 37.9% to 4.7%, recording an astonishing 87% improvement rate. From the reports above, we can conclude that there’s a strong and direct relation between phishing simulation and employees' capability to spot and report phishing emails.
4. Phishing simulations reduce possible risks (+)
- They reduce the likelihood of a security incident and breaches
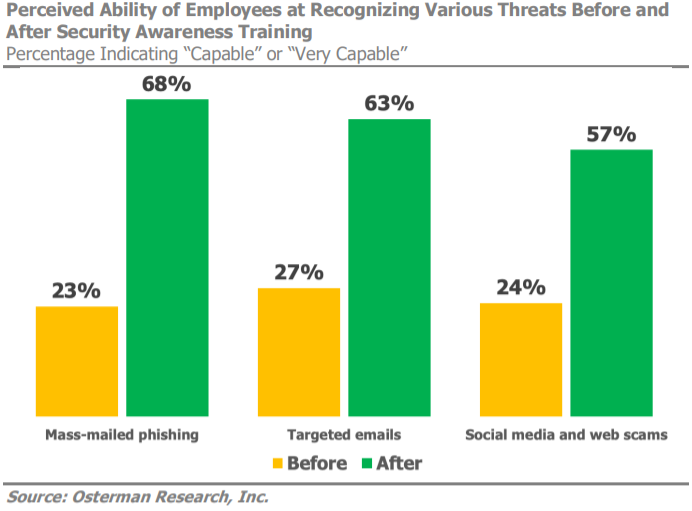
The graph below gives a visual insight into one study that measured how staff were able to recognise threats before and after training. As this shows, security awareness training makes staff much more capable of identifying potential cyber threats (Source).
- They reduce financial loss
According to IBM’s 2023 Cost of a Data Breach Report, the average cost of a data breach in the higher education and training sector was $3.65 million between March 2022 and March 2023. The mean time for all sectors to identify a data breach was 204 days with an additional 73 days on average to contain it.
These exercises will:
- Deliver periodic simulated email phishing challenges based on real life phishing attempts
- Give the University community experience in identifying and reporting phishing emails
- Provide incentives for reporting phishing challenges
- Provide an evidence-based understanding of the University’s phishing risks
These exercises will not:
- Send “gotcha” emails using messages more sophisticated than we typically receive
- Impersonate UD’s HR or Benefits departments or services
- Report the identities of those who click
- Assign mandatory training or take punitive action against those who click
What to expect
Email users should expect to receive a simulated phish once per month. Like any suspected phishing message, it should be reported by clicking the Phish Alert Button  . You will be notified that the phish was a simulation.
If you miss it and accidentally click on a link in the phishing email, you’ll see a page that reassures you it’s just practice and highlights the warning signs to watch out for next time. Close that page and report the phishing email by clicking the phish alert button message anyway. After all, it’s good practice.
. You will be notified that the phish was a simulation.
If you miss it and accidentally click on a link in the phishing email, you’ll see a page that reassures you it’s just practice and highlights the warning signs to watch out for next time. Close that page and report the phishing email by clicking the phish alert button message anyway. After all, it’s good practice.
Have Questions?
If you’d like more information on identifying phish, resources are available to you here. If you have questions, concerns, or comments about our Phish Reporting exercises, please contact the askit@udel.edu.



